MAC address filtering is one of those controversial features that some people swear by, whereas others say it’s a complete waste of time and resources. So which is it? In my opinion, it’s both, depending on what you are trying to accomplish by using it.
Dec 05, 2017 How to Hack Neighbor’s Wi-Fi Using Linux? Only real hackers can do it, using Linux OS, pyrit and some Linux tools that are called airodump-ng and aireplay-ng. To grab the password: disable Wi-Fi interface; change your mac address; collect information using the tools; start wlan0 interface; disconnect all the certain Wi-Fi users.
Unfortunately, this feature is marketed as a security enhancement that you can use if you are technically-savvy and willing to put in the effort. The real fact of the matter is that it really provides no extra security and can actually make your WiFi network less secure! Don’t worry, I’ll explain more about that below.
However, it’s not completely useless. There are some legitimate cases where you can use MAC address filtering on your network, but it won’t add additional security. Instead, it’s more of an administration tool that you can use to control whether or not your kids can access the Internet at certain times during the day or if you want to manually add devices to your network, which you can monitor.
Why It Doesn’t Make Your Network More Secure
The main reason why it doesn’t make your network more secure is because it’s really easy to spoof a MAC address. A network hacker, which can literally be anyone since the tools are so easy to use, can easily figure out the MAC addresses on your network and then spoof that address onto their computer.
So, you may ask, how can they get your MAC address if they can’t connect to your network? Well, that’s an inherent weakness with WiFi. Even with a WPA2 encrypted network, the MAC addresses on those packets are not encrypted. This means that anyone with network sniffing software installed and a wireless card in range of your network, can easily grab all the MAC addresses that are communicating with your router.
They can’t see the data or anything like that, but they don’t really have to break the encryption to access your network. Why? Because now that they have your MAC address, they can spoof it and then send out special packets to your router called disassociation packets, which will disconnect your device from the wireless network.
Then, the hackers’ device will try to connect to the router and will be accepted because it is now using your valid MAC address. This is why I said earlier that this feature can make your network less secure because now the hacker doesn’t have to bother trying to crack your WPA2 encrypted password at all! They simply have to pretend to be a trusted computer.
Again, this can be done by someone who little to no knowledge of computers. If you just Google crack WiFi using Kali Linux, you’ll get tons of tutorials on how to hack into your neighbor’s WiFi within a few minutes. So do those tools always work?
The Best Way to Stay Secure

Those tools will work, but not if you are using WPA2 encryption along with a fairly long WiFi password. It’s really important that you don’t use a simple and short WiFi password because all a hacker does when using these tools is a brute force attack.
With a brute force attack, they will capture the encrypted password and try to crack it using the fastest machine and the biggest dictionary of passwords they can find. If your password is secure, it can take years for the password to be cracked. Always try to use WPA2 with AES only. You should avoid the WPA [TKIP] + WPA2 [AES] option as it’s much less secure.
However, if you have MAC address filtering enabled, the hacker can bypass all that trouble and simply grab your MAC address, spoof it, disconnect you or another device on your network from the router and connect freely. Once they are in, they can do all kinds of damage and access everything on your network.

Other Solutions to the Problem
But some people will still say it’s so useful to control who can get on my network, especially since everyone doesn’t know how to use the tools I mentioned above. OK, that’s a point, but a better solution to control outsiders who want to connect to your network is to use a guest WiFi network.
Just about all modern routers have a guest WiFi feature that will allow you to let others connect to your network, but not let them see anything on your home network. If your router doesn’t support it, you can just purchase a cheap router and attach that to your network with a separate password and separate IP address range.
It’s also worth noting that other WiFi security “enhancements” like disabling SSID broadcasting will also make your network LESS secure, not more secure. Another one people have told me they try is to use static IP addressing. Again, as long as a hacker can figure out your network IP range, they can use any address in that range too on their machine, regardless of whether you have assigned that IP or not.
Hopefully, this gives you a clear idea of what you can use MAC addressing filtering for and what expectations to have. If you feel differently, feel free to let us know in the comments. Enjoy!
Most people now use a wi-fi network to access the internet around the home. However an unsecured network could let your neighbor’s piggyback on your broadband or worse, let hackers snoop on your activities. Luckily it’s not that difficult to harden the security of your home network. Here’s a quick step-by-step. 1 Check the router
Most people now use a wi-fi network to access the internet around the home. However an unsecured network could let your neighbor’s piggyback on your broadband or worse, let hackers snoop on your activities. Luckily it’s not that difficult to harden the security of your home network. Here’s a quick step-by-step.
1 Check the router settings
The first thing to do is open a web browser to gain access to the inner workings of your router. Every router will have its own IP address (a series of numbers like 192.168.1.1) which will take you to the router management program. The manual for the router or your broadband provider should be able to supply the right address Simply type the relevant number (with the dots) into the address field of your browser to open the router settings.
2 Set an admin user name and password
You should now see the router settings in the browser window. If it does not ask you for a user name and password this means you have never been here before. Now is the time to set these up to prevent unauthorized access to your router settings. You should find this under the heading of “user management” or similar. If the name of your network and password are still the factory defaults now is the time to change them as would-be hackers can easily look up default settings of most routers just using Google.
3 Make you router invisible by changing and hiding the SSID
The SSID (Service Center Identifier) is just a fancy technical term for the name of your own wireless network. It is what appears in the list of available networks that devices display when people are looking to join a network. By going into the SSID setting you can make your network “invisible” to anyone outside your network by disabling the “SSID broadcasting” function. Users will have to know and enter the Network Name manually if they want to connect to your wireless network. You should also rename your network from the factory default (Verizon, AT&T or similar) to something so that only authorized users will know. Don’t use your name, address or anything else that would be obvious.
4 Enable Network Encryption
You’ve made your network invisible to the outside world but you now need to scramble all the data going in and out of it to further deter hackers and snoopers. This is known as encryption and your router will have settings to allow you to do this. You will see the options for the following settings: WEP, WPA & WPA2. WEP is the least secure and WPA2 is the most advanced, unless you have older devices that require WEP, go WPA2 for as it is much harder to crack. You now need to set a password to enter your newly encrypted Wi-Fi network. Choose something long, with a mix of characters that cannot easily be guessed by a hacker.
5 Add MAC addresses
These are nothing to do with Apple computers but instead the unique code hard coded into any network device. To further secure your network you can add the MAC addresses of all authorized devices in the home – iPhones, tablets, laptops etc. – to the router’s authorized list. No other device will then be allowed on the network. You can find the MAC addresses of mobile phones and other portable devices under their network settings, though this will vary for each device. Check with the manufacturer.
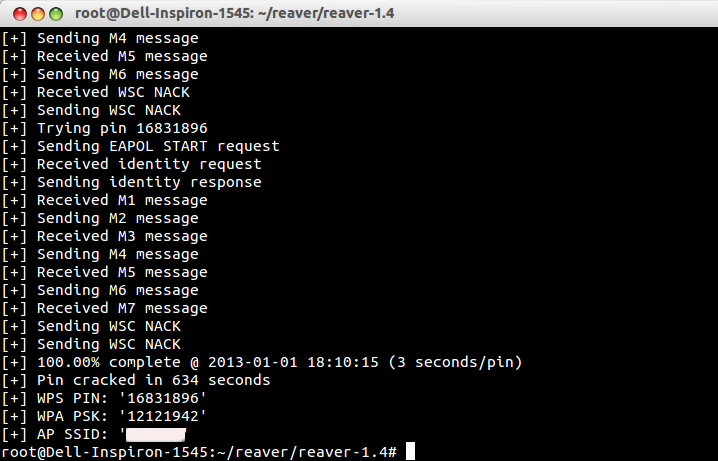
Hack Neighbors Wifi With Cmd
Hack Your Neighbors Wifi Password
Having done all this, your Wi-Fi network should now considerably more secure than it was before. If you get stuck, contact your broadband provider directly as they should be able to provide assistance.